What is the Cyber Resilience Act?
The Cyber Resilience Act (CRA) is a regulation by the European Union aimed at enhancing the cybersecurity of connected devices and software products sold within the EU. It seeks to establish clear, enforceable cybersecurity requirements for manufacturers, developers, and suppliers, ensuring that products are secure throughout their lifecycle.
Key Objectives of the CRA
1. Increase Cybersecurity Across the EU: Ensure that hardware and software products are designed and maintained with robust cybersecurity measures.
2. Mitigate Risks: Address vulnerabilities to reduce the risk of cyberattacks on consumers, businesses, and critical infrastructure.
3. Harmonize Standards: Provide a unified framework for cybersecurity standards across the EU market, reducing fragmentation.
4. Enhance Consumer Trust: Give users greater confidence in the security of connected products.
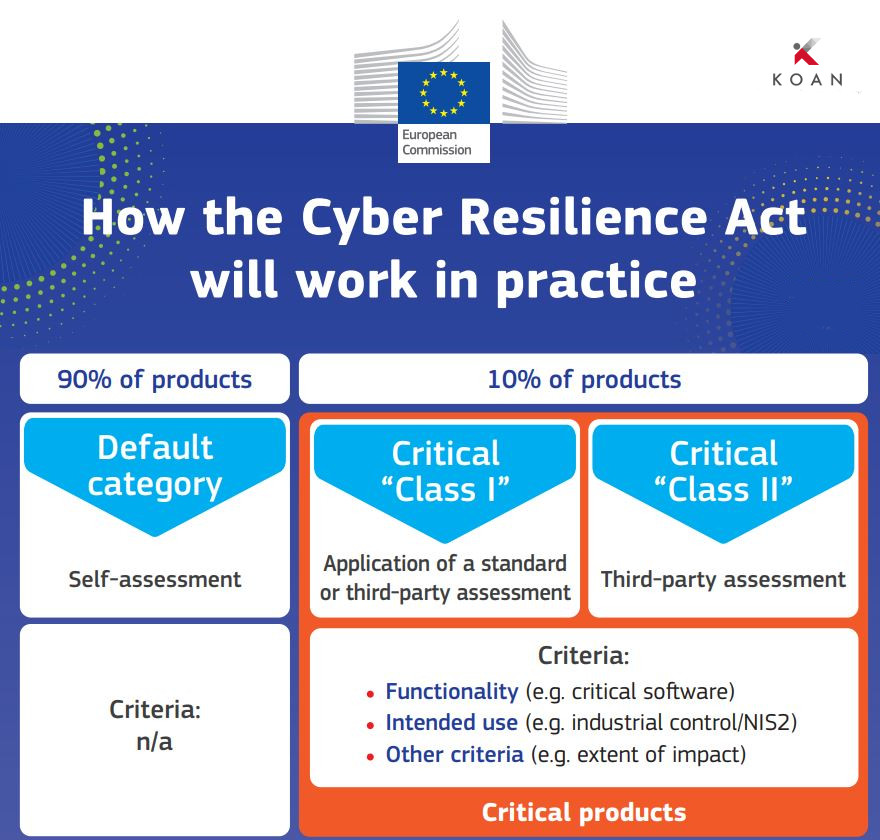
Scope of the CRA
The CRA applies to a wide range of devices and software, including:
- IoT devices (e.g., smart home appliances, wearables).
- Software products (both standalone and embedded in devices).
- Industrial equipment and critical systems.
Exclusions may include certain specialized or regulated systems, like military equipment or medical devices, which fall under other EU laws.
Key Requirements
– Security by Design: Products must be designed to minimize vulnerabilities and comply with cybersecurity best practices.
– Vulnerability Management: Manufacturers must ensure mechanisms are in place to identify, report, and address vulnerabilities throughout the product lifecycle.
– Mandatory Declarations: Businesses must provide clear information about a product’s cybersecurity features and any potential risks.
– Compliance and Penalties: Non-compliance with the CRA could lead to fines or the removal of products from the EU market.
Current Status
The Cyber Resilience Act (CRA) was published in the Official Journal of the EU (OJEU) on November 20th, 2024.
It complements existing regulations like the General Data Protection Regulation (GDPR) and the Network and Information Security Directive (NIS2). Once adopted, businesses will likely have a transition period to meet the new requirements.
The CRA underscores the EU’s focus on making cybersecurity a cornerstone of its digital policy.
Essential Cybersecurity Requirements
Refer to pages 68 and 69 (Annex I) for the “Essential Cybersecurity Requirements” applicable to all products.
The “Essential Cybersecurity Requirements” in Annex I (pages 68-69) of the Cyber Resilience Act outline fundamental obligations that manufacturers, developers, and suppliers of digital products must adhere to. These requirements are designed to ensure that all products entering the EU market are secure by design and resilient against cyber threats. Below is an overview of these requirements:
Key Cybersecurity Requirements
1. Protection Against Known Exploits:
– Products must be designed and developed to minimize risks arising from known vulnerabilities.
– Implementation of security updates to address known exploits promptly.
2. Secure Default Configurations:
– Products must be supplied with security settings enabled by default.
– Configurations should prioritize cybersecurity without requiring extensive user intervention.
3. Resilience to Attacks:
– Products must be resistant to cyberattacks that compromise functionality or expose sensitive information.
– Mechanisms to detect, prevent, and respond to attacks must be integrated.
4. Safe Communication and Data Handling:
– Ensure data transmitted or processed is adequately protected (e.g., encryption and access control).
– Products must support secure authentication and authorization protocols.
5. Minimized Attack Surface:
– Reduce unnecessary features and interfaces that could expose vulnerabilities.
– Only essential services and functions should be active by default.
6. Maintenance and Vulnerability Management:
– Products must include clear processes for monitoring, identifying, and mitigating vulnerabilities throughout their lifecycle.
– Transparency in informing users about discovered vulnerabilities and how to address them.
7. Accountability for Third-Party Components:
– Developers must ensure that third-party components integrated into products meet cybersecurity standards.
– Regular updates and risk assessments for third-party elements are required.
Specific Lifecycle Requirements
A. End-of-Support Management:
– Clear notification to users about the period during which the product will receive updates and support.
– Provide guidance on safe usage after the support period ends.
B. Incident Reporting:
– Manufacturers must notify users and relevant authorities about significant cybersecurity incidents affecting their products.
These essential requirements are mandatory for all products within the CRA’s scope. Manufacturers must document compliance and be prepared to provide evidence if audited by EU authorities.
How KOAN can help you with CRA on embedded linux?
KOAN is a specialized provider of Embedded Linux solutions particularly using the Yocto Project, and it can play a critical role in helping manufacturers comply with the Cyber Resilience Act (CRA). Here’s how KOAN’s expertise can support you in meeting the CRA’s requirements for embedded Linux systems:
1. Security by Design
– Customized Secure Yocto Linux Distributions: KOAN can develop tailored Linux distributions with built-in security features that meet CRA standards, such as secure boot, encrypted file systems, and hardened kernels.
– Secure Configuration: Ensure default configurations prioritize security, aligning with CRA requirements for “secure by default” setups.
2. Vulnerability Management
– Regular Patching and Updates: KOAN can offer commercial support to provide lifecycle management services, including proactive monitoring, vulnerability assessments, and timely distribution of security patches.
– Support for CVE Mitigation: Our commercial support may help identify and mitigate vulnerabilities in your embedded Linux system by integrating tools and processes for CVE (Common Vulnerabilities and Exposures) tracking and resolution.
3. Compliance Documentation
– SBOM (Software Bill of Materials): KOAN can generate and maintain an accurate SBOM for your Linux system, which is critical for demonstrating compliance with CRA’s requirements for transparency regarding third-party components.
– Compliance Verification: KOAN assists in documenting security measures, configurations, and processes to ensure they meet CRA specifications.
4. Secure Communication and Data Handling
– Implementation of Secure Protocols: KOAN can configure your embedded Linux system to use secure communication protocols (e.g., TLS/SSL) and data encryption.
– Access Controls: Integrate robust user authentication and authorization mechanisms. (Read our Audit guide)
5. Resilience and Incident Handling
– Hardened Linux for Attack Resilience: Implement measures like SELinux or AppArmor for added security layers to resist potential cyberattacks. (Through third party services)
– Incident Response Tools: Embed monitoring tools and logging systems to detect, respond to, and report cybersecurity incidents efficiently. (Through third party services)
6. Product Lifecycle Management
– Long-term Support (LTS): KOAN can help you establish long-term support policies for embedded Linux systems, ensuring compliance with CRA requirements for maintenance and end-of-support notifications.
– End-of-Life Planning: Assist in planning and documenting safe usage and mitigation strategies for the post-support lifecycle.
7. Training and Support
– Developer Training: KOAN offers training on secure development practices for embedded Linux, ensuring your team understands CRA-aligned cybersecurity principles. (From Q1-2025)
– Ongoing Technical Support: Continuous assistance for compliance monitoring, updates, and adapting to new CRA guidelines.
By partnering with KOAN, businesses leveraging embedded Linux can not only ensure compliance with the CRA but also build a foundation for robust, secure, and resilient products.